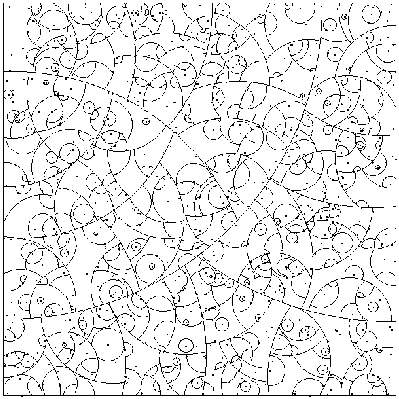Up: Publication homepage
Data Structures and Algorithms for Nearest Neighbor Search in
General Metric Spaces
Peter N. Yianilos
NEC Resarch Institute
Abstract:
We consider the computational problem of finding nearest neighbors in
general metric spaces. Of particular interest are spaces that may not
be conveniently embedded or approximated in Euclidian space, or where
the dimensionality of a Euclidian representation is very high.
Also relevant are high-dimensional Euclidian settings in
which the distribution of data is in some sense of lower dimension and
embedded in the space.
The vp-tree (vantage point tree) is introduced in several forms,
together with associated algorithms, as an improved method for these
difficult search problems. Tree construction executes in 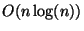 time, and search is under certain circumstances and in the
limit,
time, and search is under certain circumstances and in the
limit, 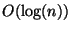 expected time.
expected time.
The theoretical basis for this approach is developed and the
results of several experiments are reported. In Euclidian cases,
kd-tree performance is compared.
Keywords: Metric Space,
Nearest Neighbor,
Computational Geometry,
Associative Memory,
Randomized Methods,
Pattern Recognition,
Clustering.
Nearest neighbor analysis is a well established technique for
non-parametric density estimation, pattern recognition,
memory-based reasoning, and vector quantization.
It is also highly intuitive notion that seems to correspond in
some way with the kind of inexact associative recall that is
clearly a component of biological intelligence.
One useful abstraction of nearness is provided by the
classical notion of a mathematical metric space
[1]. Euclidian  -space is but one example
of a metric space.
-space is but one example
of a metric space.
The Nearest Neighbor field includes the study of decision
making and learning based on neighborhoods, the underlying
metrics and spaces, and the matter of computing/searching for
the neighborhood about a point. See [2] for
a recent survey. Our focus is on search, and, for simplicity,
on locating any single nearest neighbor.
Given a fixed finite subset of the space and calling it the
database, our task is then to locate for each new query drawn from the space, a database element nearest to it.
As the database is finite, we might search by considering
every member. But in a somewhat analogous setting, binary
search can locate a queries position within a finite ordered
database while considering only 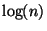 elements.
Moreover, binary search proceeds given only ordinal knowledge.
I.e., it doesn't matter what the database objects are.
elements.
Moreover, binary search proceeds given only ordinal knowledge.
I.e., it doesn't matter what the database objects are.
So while the notions of ordering and metric-distance are only
loosely analogous, we are nevertheless motivated to look for
improved search methods that depend only on the information
received through metric evaluation.
Now binary search presumes that the database has been sorted
- an 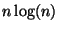 process. We then seek to organize our
database in as much time so that under some circumstances,
logarithmic time search is possible.
process. We then seek to organize our
database in as much time so that under some circumstances,
logarithmic time search is possible.
We introduce the vp-tree (vantage point tree) in several
forms as one solution. This data structure and the
algorithms to build and search it were first discovered and
implemented by the author during 1986-871 in conjunction with the development of improved retrieval
techniques relating to the PF474 device
[3].
Motivation was provided by the fact that this chip's notion
of string distance is non-Euclidian. Here elements of the
metric space are strings, E.g., a database of city names and
associated postal codes. This early work was described in
[4].
Independently, Uhlmann has reported the same basic structure
[5,6] calling it a metric tree.
There is a sizable Nearest Neighbor Search literature, and the
vp-tree should properly be viewed as related to and descended
from many earlier contributions which we now proceed to
summarize.
Burkhard and Keller in [7] present three file
structures for nearest neighbor retrieval. All three involve
picking distinguished elements, and structuring according to
distance from these members. Their techniques are coordinate
free. The data structures amount to multi-way trees
corresponding to integral valued metrics only.
Fukunaga in [8,9] exploits
the triangle inequality to reduce distance computations
searching a hierarchical decomposition of Euclidian Space. His
methods are restricted to a Euclidian setting only by his use
of a computed mean point for each subset. However this
is not an essential component of his approach - at least
conceptually. He recursively employs standard clustering
[10] techniques to effect the decomposition and
then branch-and-bound searches the resulting data structure.
During search, the triangle inequality implies that a cluster
need not be explored if the query is far enough outside of it.
While exploring a cluster at the lowest level, Fukunaga
further points out that the triangle inequality may be used to
eliminate additional distance computations. A key point
apparently overlooked, is that when the query is well inside
of a cluster, the exterior need not be searched.
Collections of graphs are considered in [11] as
an abstract metric space with a metric assuming discrete
values only. This work is thus highly related to the
constructions of [7]. In their concluding
remarks the authors correctly anticipate generalization to
more continuous settings such as
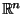 .
.
The kd-tree of Friedman and Bentley
[12,13,14,15]
has emerged as a useful tool in Euclidian spaces of moderate
dimension. Improvements relating to high-dimensional
settings, distribution adaptation, and incremental searches,
are described in [16], [17], and
[18] respectively.
A kd-tree is built by recursively bisecting the database
using single coordinate position cuts. For a given
coordinate, the database is cut at the median of the
distribution generated by projection onto that coordinate. An
optimized kd-tree results by choosing the cutting
coordinate to be that whose distribution exhibits the most
spread.
In addition to various vp-tree forms, we have implemented
optimized kd-tree software so that experimental comparisons
can be made operating on identical spaces and given identical
query sequences.
Like the kd-tree, each vp-tree node cuts/divides the
space. But rather than using coordinate values, a vp-tree
node employs distance from a selected vantage point. Near
points make up the left/inside subspace while the right/outside subspace consists of far points. Proceeding
recursively, a binary tree is formed. Each of its nodes
identifies a vantage point, and for its children
(left/right), the node contains bounds of their associated
subspace as seen by the vantage point. Other forms of the
vp-tree include additional subspace bounds and may employ buckets near leaf level.
To build these structures, the metric space is decomposed
using large spherical cuts centered in a sense at elements
near the corners of the space. This contrasts with the
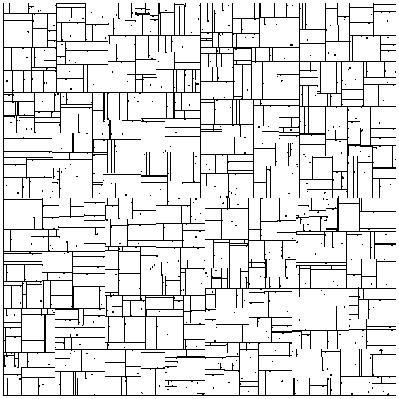
coordinate aligned hyperplanar cuts of the kd-tree (See
Figures 1 & 2), and
the use of computed Euclidian cluster centroids in
[8]. Randomized algorithms for vp-tree
construction execute in
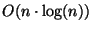 time and the
resulting tree occupies linear space.
time and the
resulting tree occupies linear space.
Figure 1:
vp-tree decomposition
|
Figure 2:
kd-tree decomposition
|
For completeness, early work dealing with two special cases
should be mentioned. Retrieval of similar binary keys is
considered by Rivest in [19] and the 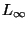 (max) metric setting is the focus of [20].
(max) metric setting is the focus of [20].
More recently, the Voronoi digram [21] has
provided a useful tool in low- dimensional Euclidian settings
- and the overall field and outlook of Computational Geometry
has yielded many interesting results such as those of
[22,23,24,25] and
earlier [26].
Unfortunately neither the kd-tree, or the constructions of
computational geometry, seem to provide a practical solution
for high dimensions. As dimension increases, the kd-tree
soon visits nearly every database element while other
constructions rapidly consume storage space.
Furthermore, even if the database is in some sense of
only moderately high dimension, it may not be possible or
convenient to find or implement a dimension reducing
transformation. So it is important that we develop
techniques that can deal with raw untransformed data, and
exhibit behavior as close as possible to intrinsic rather
than representational dimension.
So despite considerable progress for Euclidian space, the
development of more general techniques is important; not just
because of the problems with high dimension, but also because
there is no a priori reason to believe that all or even most
useful metrics are Euclidian.
In the sections that follow we will consider a probabilistic
formulation of the problem and obtain certain theoretical
results, present the algorithms and data structures for the
vp-tree in several forms, and report on a number of
experiments. These experiments include Euclidian cases with
side-by-side kd-tree comparisons, non-Euclidian spaces, and
the difficult real-world problem of image fragment
retrieval. Here fragments as large as 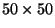 pixels
are treated corresponding to representational dimension
pixels
are treated corresponding to representational dimension 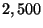 .
.
In this section we develop a simple but fairly general result
which says that under certain circumstances, one may organize
a database so that expected search time is logarithmic. It
should be thought of as justifying in the limit the
algorithms and data structures presented later.
Only elementary concepts from General Topology and
Measure/Probability Theory are employed.
Given a metric space 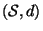 and some finite subset
and some finite subset
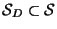 representing the database against which
nearest neighbor queries are to be made, our objective is to
somehow organize
representing the database against which
nearest neighbor queries are to be made, our objective is to
somehow organize 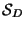 so that nearest neighbors may be
more efficiently located.
so that nearest neighbors may be
more efficiently located.
For a query
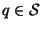 , the nearest neighbor problem
then consists of finding a single minimally distant member of
, the nearest neighbor problem
then consists of finding a single minimally distant member of
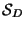 . We may write
. We may write
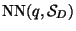 to stand for this
operation where the space may be omitted for brevity.
to stand for this
operation where the space may be omitted for brevity.
Now the element nearest to 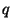 may be quite far, and for a
particular problem it may be reasonable to impose a distance
threshold
may be quite far, and for a
particular problem it may be reasonable to impose a distance
threshold 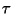 , at or beyond which one is uninterested in
the existence of neighbors. Also observe that while computing
, at or beyond which one is uninterested in
the existence of neighbors. Also observe that while computing
 , one may by reduce
, one may by reduce  as ever nearer neighbors
are encountered. We write
as ever nearer neighbors
are encountered. We write
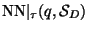 to denote this
important notion of
to denote this
important notion of 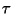 restricted search.
restricted search.
Next we will assume that the range of the space's distance
distance function is ![$[0,1]$](img28.gif) . Since any metric's range may
be compressed to this interval without affecting the
nearest-neighbor relation2, this restriction may be made without loss of generality3.
. Since any metric's range may
be compressed to this interval without affecting the
nearest-neighbor relation2, this restriction may be made without loss of generality3.
Each element of a metric space has in a sense a perspective on the entire space; formed by considering its
distances to every other element. This perspective need not
however contain any information. Consider the
pathological case of the discrete metric in which the distance
between any pair of distinct points is one. Here, full-space
search is unavoidable. However, to the extent that information is
present, we will see that nearest neighbor search may benefit.
We begin by formalizing this notion of perspective and defining
a related pseudo-distance function:
Function 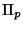 is best thought of as a projection of
is best thought of as a projection of
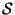 into
into ![$[0,1]$](img28.gif) , from the perspective of
, from the perspective of 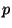 . I.e. it
is
. I.e. it
is 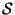 as seen by
as seen by 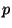 , via
, via 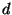 . Function
. Function 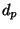 is
not in general a metric since if
is
not in general a metric since if 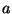 and
and 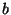 are distinct but
equidistant from
are distinct but
equidistant from 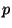 ,
, 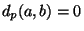 . It is however a clearly
symmetric function and satisfies the triangle inequality,
making it a pseudo-metric.
. It is however a clearly
symmetric function and satisfies the triangle inequality,
making it a pseudo-metric.
Now since 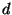 is a metric we may rely on symmetry and the
triangle inequality to arrive at:
is a metric we may rely on symmetry and the
triangle inequality to arrive at:
Hence, distances shrink when measured by 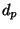 so that
so that
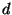 in a sense dominates it. One useful consequence of this
behavior is given by the following obvious implication:
in a sense dominates it. One useful consequence of this
behavior is given by the following obvious implication:
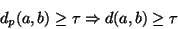 |
(1) |
So if during a search we've already encountered a database
element 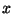 at distance
at distance 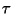 from
from 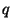 , then as our search
progresses, we need not consider any element for which
, then as our search
progresses, we need not consider any element for which
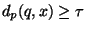 . Thus, in the absence of coordinates or
Euclidian structure, we can begin to see how query's distance
to a distinguished vantage point may be exploited to
effectively direct and limit the search.
. Thus, in the absence of coordinates or
Euclidian structure, we can begin to see how query's distance
to a distinguished vantage point may be exploited to
effectively direct and limit the search.
For some
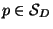 consider now the image
consider now the image
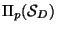 of
of 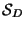 in
in ![$[0,1]$](img28.gif) . Next denote by
. Next denote by 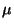 the median of
the median of
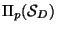 thus dividing
thus dividing ![$[0,1]$](img28.gif) into
into 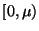 and
and
![$[\mu,1]$](img49.gif) . The first of these intervals contains points from
the inside the sphere
. The first of these intervals contains points from
the inside the sphere 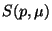 , while the second consists of
points from outside and on the surface. We denote the inverse
images of these
, while the second consists of
points from outside and on the surface. We denote the inverse
images of these 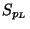 and
and 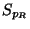 respectively; and
imagine that
respectively; and
imagine that 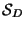 is divided in this way into left
and right subspaces.
is divided in this way into left
and right subspaces.
Now
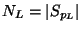 counts the points of
counts the points of 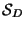 mapped
left to
mapped
left to 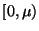 , while
, while
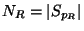 counts those
sent right to
counts those
sent right to ![$[\mu,1]$](img49.gif) . We can say little in general
about the comparative sizes of
. We can say little in general
about the comparative sizes of 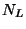 and
and 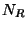 since nothing
has been assumed about the nature of the metric space. In
particular if there are many points of
since nothing
has been assumed about the nature of the metric space. In
particular if there are many points of 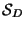 exactly
distance
exactly
distance 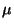 from
from 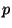 , then
, then 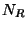 may be much larger than
may be much larger than
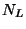 .
.
But if spheres in
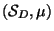 typically have on their
surface relatively few members of
typically have on their
surface relatively few members of 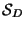 , then we can say
that
, then we can say
that
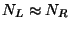 , i.e, we have partitioned
, i.e, we have partitioned 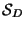 into
two subsets of roughly equal size.
into
two subsets of roughly equal size.
Now suppose for a given 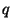 , that our objective is
, that our objective is
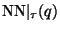 ,
and that
,
and that
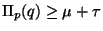 . Then it follows from
EQ- 1 that
. Then it follows from
EQ- 1 that 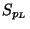 may be excluded from
consideration. Similarly if
may be excluded from
consideration. Similarly if
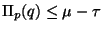 , we
may ignore
, we
may ignore 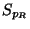 . In both cases then, roughly half the
space is excluded from consideration. Thus, the information
gleaned from a single point's perspective is sometimes
sufficient to significantly prune the search. However if
. In both cases then, roughly half the
space is excluded from consideration. Thus, the information
gleaned from a single point's perspective is sometimes
sufficient to significantly prune the search. However if
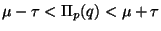 , then no such reduction
is possible.
, then no such reduction
is possible.
So it is clear that our ability to prune is dependent on a
fortuitous choice of 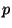 and
and 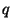 , on
, on 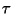 , and on our
ability to choose
, and on our
ability to choose
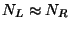 . We will succeed to the
extent that it is improbable that
. We will succeed to the
extent that it is improbable that
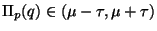 (Figure 3).
(Figure 3).
If our probability distribution is in some sense nice
(see §2.3), then we can make this probability
approach zero as 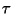 does. So that for
does. So that for 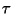 sufficiently
small, we will with high probability exclude approximately
half of the space from consideration.
sufficiently
small, we will with high probability exclude approximately
half of the space from consideration.
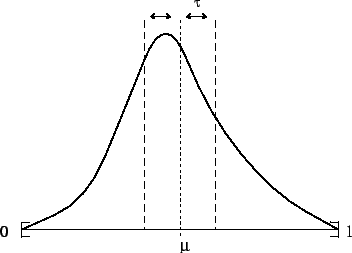
Figure 3:
A continuous rendering of the density of
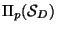 in [0,1] - and a
in [0,1] - and a 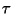 neighborhood of median
neighborhood of median 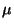
|
It is easy now to see how we may recursively proceed to form a
binary tree. This then forms the most basic vp-tree. Specific construction and search algorithms are
presented in §3.
Since individual instances of finite metric spaces (databases)
may be pathological for nearest neighbor search, we are led to
formulate the problem in probabilistic terms and seek expected
time results.
We therefore define probability measure 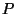 which we
assume reflects the distribution from which both database
elements and queries are drawn4. It is worthwhile noting that
the arguments that follow may be generalized to deal with
separate distributions.
which we
assume reflects the distribution from which both database
elements and queries are drawn4. It is worthwhile noting that
the arguments that follow may be generalized to deal with
separate distributions.
Now from EQ- 1 it is clear that mapping
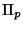 is uniformly continuous, from which it follows that the
inverse images of any point or interval (whether open, closed,
or half-open) must have defined probability.
is uniformly continuous, from which it follows that the
inverse images of any point or interval (whether open, closed,
or half-open) must have defined probability.
Thus, given some such point or interval 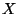 , we may for the
sake of notational simplicity refer to
, we may for the
sake of notational simplicity refer to 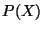 which is
understood to mean
which is
understood to mean
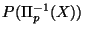 . So if
. So if ![$x \in
[0,1]$](img69.gif) , then
, then 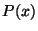 is the probability of the surface of
sphere
is the probability of the surface of
sphere 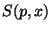 .
.
Now in the case of the discrete metric, there is about every
point a spherical surface of probability one. This is in
stark contrast to Euclidian settings where any volume related
probability measure results in zero probability spherical surfaces.
Remembering that the discrete metric is
pathological to nearest neighbor schemes, we are led to
consider metrics which share this property.
The discrete metric is thus excluded along with many other
cases. This is however a very strong condition. We assume it
for simplicity's sake but comment that there are several ways
to weaken it while preserving the essence of the arguments
that follow.
The probability of a countable intersection of nested sets,
is just the limit of the individual probabilities. This and
ZPS then imply that about any ![$x \in
[0,1]$](img69.gif) , there exists an
interval of arbitrarily small probability. Nothing more than
this basic observation is necessary to establish the two
simple theorems that follow. It is however worth remarking
that uniform convergence to zero probability can be
established. I.e., given
, there exists an
interval of arbitrarily small probability. Nothing more than
this basic observation is necessary to establish the two
simple theorems that follow. It is however worth remarking
that uniform convergence to zero probability can be
established. I.e., given 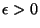 , there exists
, there exists 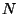 sufficiently large, so that every interval of the canonical
sufficiently large, so that every interval of the canonical
![$[0,1]$](img28.gif)
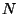 -partitioning, has probability less than
-partitioning, has probability less than
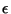 .
.
We now make more rigorous our earlier comments regarding
procedures for recursive space bisection.
Theorem 1
Let
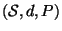
, be a
![$[0,1]$](img28.gif)
bounded metric space
with the ZPS property under probability measure
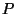
.
Then except for cases of probability zero, every
size
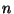
database
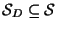
drawn from
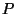
, may be organized into a binary tree; so that
given
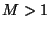
, and queries `
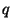
' drawn from
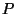
,
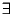
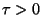
such that
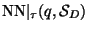
may be
computed using at most
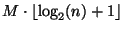
metric evaluations on an expected basis.
proof: Let
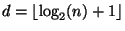 and if
and if 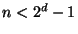 draw additional elements until equality.
draw additional elements until equality.
Pick some
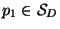 and consider
and consider
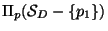 . Set value
. Set value 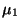 so that
equally many image points are to its left and right.
Continue recursively bisecting the space - forming a
binary tree and establishing
so that
equally many image points are to its left and right.
Continue recursively bisecting the space - forming a
binary tree and establishing 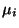 for each non-leaf
element of
for each non-leaf
element of 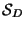 . By ZPS this is almost always
possible (failure probability zero).
. By ZPS this is almost always
possible (failure probability zero).
Define
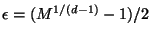 so
so
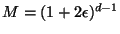 .
.
Associate with 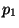 values
values
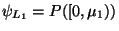 and
and
![$\psi_{R_1} = P([\mu_1,1])$](img93.gif) . Now by
our earlier comments we may choose
. Now by
our earlier comments we may choose 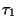 such that
such that
![$P([\mu_1-\tau_1,\mu_1+\tau_1]) < \epsilon$](img95.gif) .
.
In what follows we will proceed recursively to
associate 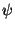 and
and 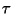 values to each non-leaf
node.
values to each non-leaf
node.
The root's probability function is just 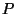 . We
define that of its left child to be essentially
. We
define that of its left child to be essentially
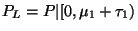 but more formally
but more formally
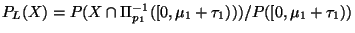 .
.
To understand this observe that
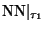 search
will explore leftward only if
search
will explore leftward only if
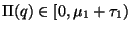 . An alternative view is that the
left subtree is only concerned with the subspace
. An alternative view is that the
left subtree is only concerned with the subspace
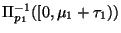 and sees it
as the entire space. In a similar way we associate a
new probability function with the right child. Now it
must be noted that these modified functions remain
probability measures, and inherit ZPS.
and sees it
as the entire space. In a similar way we associate a
new probability function with the right child. Now it
must be noted that these modified functions remain
probability measures, and inherit ZPS.
Having done this, 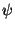 and
and 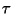 values may be
associated with the left and right child. This
enables the process to continue down the tree until
all non-leaf nodes have values. Finally set
values may be
associated with the left and right child. This
enables the process to continue down the tree until
all non-leaf nodes have values. Finally set
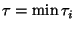 .
.
For a query 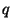 drawn by
drawn by 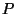 , We compute
, We compute
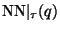 starting at the root. Thus a single metric evaluation
is always performed. Then with probability of no more
than
starting at the root. Thus a single metric evaluation
is always performed. Then with probability of no more
than
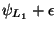 , we will be required to
explore leftward. The probability of rightward
exploration is similarly bounded by
, we will be required to
explore leftward. The probability of rightward
exploration is similarly bounded by
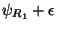 . In both cases the subtrees
will see the query as random within their
subspaces of interest.
. In both cases the subtrees
will see the query as random within their
subspaces of interest.
If leaf level is reached, a single evaluation is
always performed. It then follows that the overall
cost (metric evaluations) of the search is on an
expected basis is the value 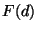 where
where 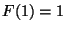 and
and
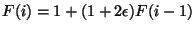 . This recursion
evaluates to
. This recursion
evaluates to
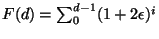 which
is bounded above by
which
is bounded above by
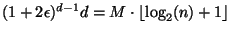


A result similar in flavor may be proven in which a tree is
built and used to classify additional members of the space so
that all buckets (leaf levels) have equal probability. Each
of these leaves then correspond to a subspace of the metric
space and we have in effect then equipartitioned the space with
respect to the probability distribution. This is analogous to
vector quantization in Euclidian space. Thinking of the
root-leaf path as a binary code, we might also interpret it as
metric space hashing.
Theorem 2
Let
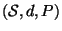
, be a
![$[0,1]$](img28.gif)
bounded metric space
with the ZPS property under probability measure
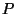
.
Then for any fixed database size
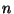
, and
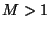
,
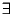
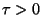
such that we may compute
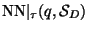
with at most
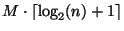
expected metric evaluations; as
databases
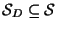
and queries `
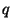
'
are drawn from
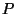
.
proof: For brevity's sake assume 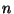 is a power of 2. As in
the previous theorem we will build a binary tree.
Before we were forced to bisect a particular finite
database at each level so that in general
is a power of 2. As in
the previous theorem we will build a binary tree.
Before we were forced to bisect a particular finite
database at each level so that in general
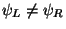 . Here we begin by building a balanced binary
tree so that its initial
. Here we begin by building a balanced binary
tree so that its initial
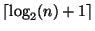 levels
have
levels
have
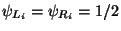 . We may do this
by picking for the root an arbitrary element, then
setting the root's
. We may do this
by picking for the root an arbitrary element, then
setting the root's 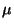 so that
so that 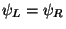 .
Having done this we may pick a vantage point for the
left and right children from the associated subspaces
and proceed recursively to the required depth.
.
Having done this we may pick a vantage point for the
left and right children from the associated subspaces
and proceed recursively to the required depth.
Observe that the leaf level subspaces have equal
probability of 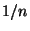 . As for
theorem- 1 we may find
. As for
theorem- 1 we may find 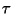 for this tree so that we expect to visit at most
for this tree so that we expect to visit at most
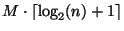 nodes. So clearly no more
than this number of leaf nodes will be visited on an
expected basis.
nodes. So clearly no more
than this number of leaf nodes will be visited on an
expected basis.
Now each element of a particular drawn database may
be classified and then attached to this
tree by first identifying which of the 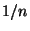 leaf
partitions it belongs to, and adding it to an
initially empty list rooted at and replacing the
corresponding leaf node. The expected size of each
list is clearly one. So the final expected number of
metric evaluations remains
leaf
partitions it belongs to, and adding it to an
initially empty list rooted at and replacing the
corresponding leaf node. The expected size of each
list is clearly one. So the final expected number of
metric evaluations remains
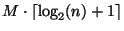 .
.


These theorems describe binary constructions to motivate the
algorithms and experiments which follow; but higher degree
trees may be built by further partitioning ![$[0,1]$](img28.gif) . In the
extreme case the root has degree
. In the
extreme case the root has degree 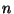 and only three metric
evaluations are expected. As a practical matter however, the
and only three metric
evaluations are expected. As a practical matter however, the
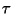 values necessary to approach even
values necessary to approach even 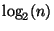 search
are so small as to be of little practical value. So the
basic theorems presented are best thought of as existence
results which establish a theoretical foundation while
motivating algorithm development.
search
are so small as to be of little practical value. So the
basic theorems presented are best thought of as existence
results which establish a theoretical foundation while
motivating algorithm development.
Now it is fairly clear that we'd like 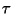 as large as
possible; and its value depends on
as large as
possible; and its value depends on 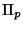 and hence on
and hence on 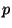 .
This then suggests that some elements of the space may be better vantage points than others. We are thus lead to
consider the problem of selecting a vantage point.
.
This then suggests that some elements of the space may be better vantage points than others. We are thus lead to
consider the problem of selecting a vantage point.
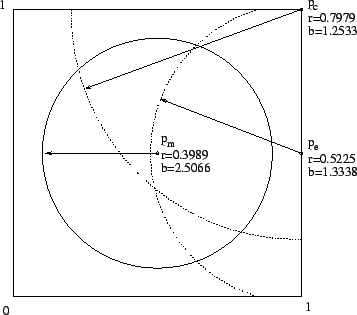
As an example consider the unit square with uniform
probability distribution. Here we must choose 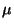 so that
two regions of area
so that
two regions of area 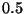 result. Three natural choices for
result. Three natural choices for
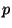 consist of the square's midpoint (denoted
consist of the square's midpoint (denoted 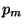 ), a corner
(denoted
), a corner
(denoted 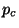 ), and the midpoint of an edge (denoted
), and the midpoint of an edge (denoted 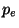 ).
These along with their associated division boundaries are
illustrated in Figure 4.
).
These along with their associated division boundaries are
illustrated in Figure 4.
Figure 4:
Natural choices for 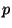 to divide the unit square
to divide the unit square
|
To choose among them, notice that for small 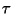 the length
of the boundary will be proportional in the limit to the
probability that no pruning takes place. Thus minimizing
these boundary lengths (denoted
the length
of the boundary will be proportional in the limit to the
probability that no pruning takes place. Thus minimizing
these boundary lengths (denoted 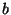 in the figure) is the
obvious strategy.
in the figure) is the
obvious strategy.
Observe that 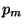 is by far the worst choice as its boundary
length is double that of
is by far the worst choice as its boundary
length is double that of 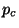 . Choice
. Choice 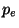 is also much
better than
is also much
better than 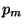 , but not quite as good as
, but not quite as good as 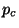 . It is
interesting to note that from a traditional clustering
viewpoint,
. It is
interesting to note that from a traditional clustering
viewpoint, 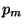 is the natural centroid. But we have seen
that it is far from the best choice. From this example we
draw the intuition that points near the corners of the
space make the best vantage points. (See again the vp-tree
decomposition of Figure- 1).
is the natural centroid. But we have seen
that it is far from the best choice. From this example we
draw the intuition that points near the corners of the
space make the best vantage points. (See again the vp-tree
decomposition of Figure- 1).
These simple results then suggest a strategy for vantage point
selection, and given a particular distribution, provide a
framework for drawing more conclusions.
The ZPS distribution restriction is key to achieving them;
and our overall outlook in which finite cases are
imagined to be drawn from a larger more continuous space,
distinguishes in part this work from the discrete distance
setting of [7,11].
We have seen that a single distinguished element 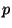 , induces a
pseudo-metric
, induces a
pseudo-metric 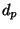 , which is always dominated by
, which is always dominated by 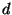 . More
generally, we observe that each size
. More
generally, we observe that each size 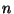 finite subset
finite subset 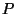 of
a metric space, considered as vantage points, induces a
natural mapping into Euclidian n-space. I.e. the
of
a metric space, considered as vantage points, induces a
natural mapping into Euclidian n-space. I.e. the 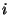 -th
coordinate of the image of
-th
coordinate of the image of 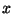 , is just
, is just 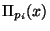 .
.
Under 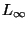 then, distances in the Euclidian range space
are always dominated by distances in the domain. This amounts
to Euclidian approximation of the original metric.
This mapping and elementary observation will help us later
define enhanced forms of the vp-tree.
then, distances in the Euclidian range space
are always dominated by distances in the domain. This amounts
to Euclidian approximation of the original metric.
This mapping and elementary observation will help us later
define enhanced forms of the vp-tree.
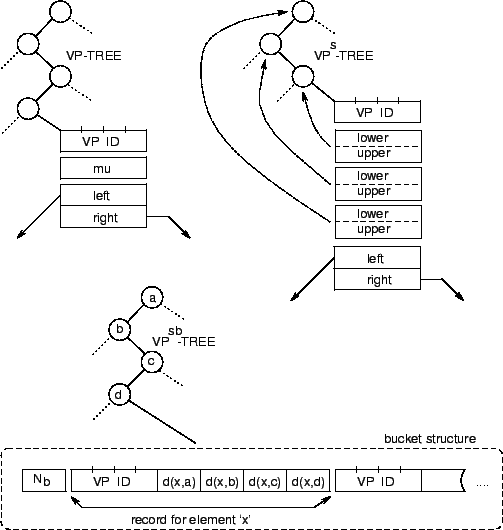
Algorithms and Data Structures.
We begin by presenting a simple algorithm for vp-tree
construction. The root corresponds to the entire space. Its
distinguished vantage point then splits the space
into left and right subspaces corresponding to the root's
left and right tree descendants. Similarly, each node is
thought of as corresponding to an ever smaller subset of the
database.
An optimized tree results because function Select_vp endevours to pick better than random vantage
points. Replacing it with a simple random selection generates
a valid and effective tree; but experiments have shown that
some effort towards making better choices, results in
non-trivial search-time savings.
Our algorithm constructs a set of vantage point candidates by random
sampling, and then evaluates each of them.
Evaluation is accomplished by extracting another sample, from
which the median of
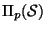 , and a corresponding moment
are estimated. Finally, based on these statistical images, the candidate with the largest moment is chosen.
Given constant size samples, execution time is
, and a corresponding moment
are estimated. Finally, based on these statistical images, the candidate with the largest moment is chosen.
Given constant size samples, execution time is 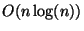 .
Our experimental implementation includes several sampling and
evaluation parameters.
.
Our experimental implementation includes several sampling and
evaluation parameters.
In the simple construction above, only mu is retained in
a node to describe the metric relationship of the left/right
subspaces to the node's vantage point. At the expense of
storage space, one may retain instead four values representing
lower/upper bounds of each subspace as seen by
the vantage point. It is this form of tree that is actually
used in the experiments we later report.
Now notice that in the course of execution, an element of
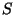 is compared with the vantage point belonging to each of
its ancestors in the tree. This information is also not
captured in the simple tree described above. Retaining it in
a particular way results in a
is compared with the vantage point belonging to each of
its ancestors in the tree. This information is also not
captured in the simple tree described above. Retaining it in
a particular way results in a
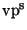 -tree - the
construction of which we now describe.
-tree - the
construction of which we now describe.
The central working structure employed consists of a database
element identifier `id', and a list `hist' of
distances from the item to each vantage point tracing back to
the root. A list of these structures is initialized from the
entire database, with the history set to null. The algorithm
then recursively splits the list into two lists 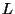 and
and 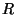 ,
while adding to the history of each item. Each resulting tree
node then contains a list `bnds' giving lower and upper
bounds (a range interval) for its corresponding subspace as
seen by each ancestral vantage point.
,
while adding to the history of each item. Each resulting tree
node then contains a list `bnds' giving lower and upper
bounds (a range interval) for its corresponding subspace as
seen by each ancestral vantage point.
Execution time remains 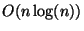 . Assuming fixed
precision is used to represent the bounds, the tree occupies
linear space. But this is an asymptotic statement, and over
the practical range of
. Assuming fixed
precision is used to represent the bounds, the tree occupies
linear space. But this is an asymptotic statement, and over
the practical range of 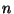 , and given fixed machine word
sizes, the space is better described by
, and given fixed machine word
sizes, the space is better described by 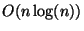 .
.
There's no guaranty that these algorithms build a balanced
tree7 - for in practice, the ZPS assumption may not
hold. Furthermore, even if it does, we may draw a rather
pathological database. So in the end, the balance achieved is
problem dependent.
Our constructions so far have involved a single node
structure. We now consider one way to form buckets of
leaves in order to save space while preserving the notion of
ancestral history present in the
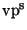 -tree. Buckets are formed
by collapsing subtrees near leaf level into a flat structure.
Each bucket contains say
-tree. Buckets are formed
by collapsing subtrees near leaf level into a flat structure.
Each bucket contains say 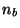 element records. Each record
must specify an id, and in addition holds distance
entries for every ancestor. We call the resulting structure a
element records. Each record
must specify an id, and in addition holds distance
entries for every ancestor. We call the resulting structure a
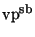 -tree. In our implementation the bucket distance values are
quantized so as to occupy only 2-bytes.
-tree. In our implementation the bucket distance values are
quantized so as to occupy only 2-bytes.
One may think of these vectors of distances, as the image of an
element under the set perspective mapping defined by
the ordered set of its ancestors. (§2.6)
The data structures corresponding to these three tree types
are depicted in Figure- 5. Database
elements are represented by a 4-byte integer, real values by a
4-byte float, and bucket distances by a 2-byte integer. These
correspond closely to our experimental implementation; except
that the
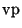 -tree we implement contains subspace bounds rather
than the single value mu.
-tree we implement contains subspace bounds rather
than the single value mu.
Figure:
Sample 32-bit machine data structure
implementations for the most basic vp-tree, the
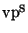 -tree, and the
-tree, and the
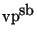 -tree.
-tree.
|
We present a single search algorithm which describes search in
a vp-tree where a node contains subspace bounds for each
child. The algorithm is easily generalized to the other tree
forms. It is a straightforward recursive branch-and-bound
tree search in which variable tau keeps track of the
closest neighbor yet encountered. Subtrees are then pruned
when the metric information stored in the tree suffices to
prove that further consideration is futile. I.e.,
cannot yield a strictly closer neighbor.
Notice that the order of exploration is determined by
comparison with the middle value computed. This is
properly viewed as a heuristic. In high dimensions this may
not be the best choice and branching order represents an
interesting area for future work.
Actual databases, particularly those consisting of signals or
images, frequently contain large clusters of very
similar items. In these cases one may find that search
rapidly locates a very near neighbor, and then performs much
more work which yields only a very slightly nearer item.
Because of this problem, our implementation includes an
error tolerance setting which in effect narrows intervals
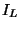 and
and 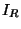 . E.g. Given tolerance 0.01, the procedure
will return a neighbor which is guaranteed to be at most 0.01
more distant from the query than its true nearest neighbor.
. E.g. Given tolerance 0.01, the procedure
will return a neighbor which is guaranteed to be at most 0.01
more distant from the query than its true nearest neighbor.
Now having summarized and sketched our algorithms and data
structures, we turn to experimental results.
A modular software system was built with plug-in metric spaces and
search routines. Two basic metric space settings were implemented:
hypercubes, and image fragments. Both support various metrics
including the standard Minkowski family.
We very nearly reproduce certain of the experimental settings from
[13] and use them to begin our process of evaluation.
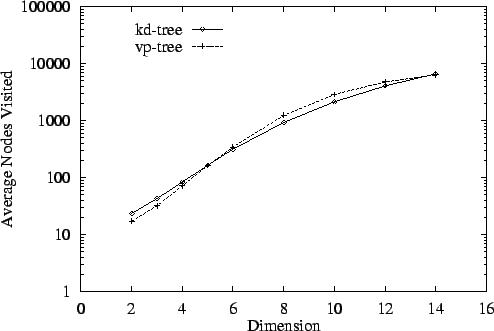
Hypercubes of increasing dimension are first considered, each
containing a database consisting of 8,192 coordinate-wise normally
distributed pseudorandom points.
The vp-tree8 and kd-tree are compared for the 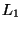 ,
, 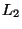 , and
, and
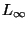 metrics as dimension ranges from 2 to 14. Since interior
vp-tree nodes contain data elements while the kd-tree contains data
elements at its leaf level only, we use total nodes visited to measure
complexity. The resulting statistics were observed to agree well with
actual CPU time used.
metrics as dimension ranges from 2 to 14. Since interior
vp-tree nodes contain data elements while the kd-tree contains data
elements at its leaf level only, we use total nodes visited to measure
complexity. The resulting statistics were observed to agree well with
actual CPU time used.
Figure 6 demonstrates the remarkable agreement
between these two methods for the 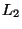 metric. Similar agreement is
found for the
metric. Similar agreement is
found for the 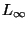 metric, while for
metric, while for 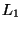 , the vp-tree maintains
a small constant advantage. Detailed examination of the results does
however reveal one qualitative difference which increases with
dimension. By dimension 14, the kd-tree visits roughly
, the vp-tree maintains
a small constant advantage. Detailed examination of the results does
however reveal one qualitative difference which increases with
dimension. By dimension 14, the kd-tree visits roughly 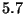 times as
many nodes under
times as
many nodes under 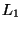 versus
versus 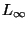 . The ratio for vp-tree
search is only
. The ratio for vp-tree
search is only 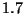 . This suggests that vp-tree performance may be
flatter with respect to choice of metric.
. This suggests that vp-tree performance may be
flatter with respect to choice of metric.
Figure 6:
Search Cost vs. Dimension Comparison For 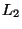 Metric and Based on Nodes Visited
Metric and Based on Nodes Visited
|
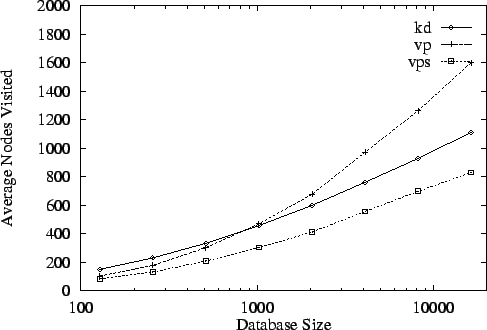
If dimension is fixed and database size grows, we expect and find
asymptotically logarithmic growth in search time. For dimension 8 (Figure
7), kd-tree performance is in the limit between that of
the vps-tree and vp-tree. Examining CPU time, the same is true although the
differences are smaller. In dimensions 2 and 4, the performance ordering
from best to worst is vps-tree, vp-tree, then kd-tree for all database
sizes.
Figure 7:
Search Cost vs. Database Size - Dimension 8
|
The kd-tree does however eventually catch up in this random
hypercube environment. By dimension 12 for example, it visits fewer
nodes than vps-tree search once database size grows beyond 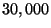 .
By this point however, neither perform very well - visiting roughly
.
By this point however, neither perform very well - visiting roughly
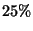 of the nodes.
of the nodes.
So despite their ignorance of the coordinate structure of the space,
and randomized construction, vp-trees compare well in this setting
with the kd-tree.
Comparisons with the experiments of [8] are more
difficult because leaf level buckets are employed. Nevertheless, based
purely on metric evaluations, the kd-tree and vp/
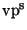 -tree methods
produce superior results.
-tree methods
produce superior results.
As a simple embedding model, we construct random linear rotation matrices
which correspond to isometric embeddings of
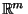 into
into
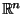 where
where 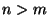 .
.
Pseudorandom databases are then drawn in a coordinate-wise uniform fashion
within
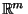 and mapped to the longer vectors of
and mapped to the longer vectors of
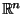 .
.
To study this setting we define three types of query distribution - all pseudo-random
but confined to different subspaces:
- T1:
- Drawn in
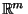 and then mapped to
and then mapped to
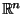 .
.
- T2:
- Drawn in
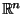 .
.
- T3:
- Drawn in
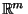 , mapped, and then combined with
, mapped, and then combined with
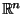 noise
having maximum amplitude
noise
having maximum amplitude 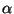 .
.
The first two of these are fairly clear; the third requires
explanation. It is proposed as a better model for the independent
effects of subspace and observational error.
We first embed a plane into 10-dimensional space (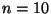 ,
, 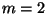 ) and
draw a 2,000 element database. Table 1 contains the
results. The values shown are average nodes visited. Its first and
last columns contain for comparison purposes, performance for fully-
random 2 and 10 dimensional hypercubes. The
`
) and
draw a 2,000 element database. Table 1 contains the
results. The values shown are average nodes visited. Its first and
last columns contain for comparison purposes, performance for fully-
random 2 and 10 dimensional hypercubes. The
`
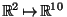 ' columns contain results for a 2-dimensional space embedded in 10-space given
types 1 and 2 queries.
' columns contain results for a 2-dimensional space embedded in 10-space given
types 1 and 2 queries.
Table 1:
Basic Embedding Search Example
| |
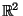 |
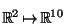 |
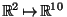 |
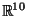 |
| |
|
Type 1 |
Type 2 |
|
| kd |
21 |
31 |
3833 |
816 |
| vp |
15 |
15 |
279 |
1048 |
| vps |
12 |
12 |
246 |
698 |
|
All trees perform well given type 1 queries and degrade for type 2. But
notice that the kd-tree searches nearly every node 9 when presented with type 2 queries. In fact, its performance is
markedly worse that in the fully random 10-dimensional setting. This
illustrates the weakness of coordinate-based schemes and the pitfalls of
assuming that random cases are indicative in any way of overall performance.
If this same database is now embedded into ever higher dimensions (3
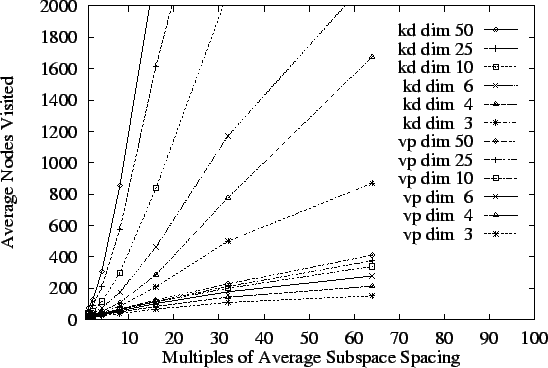
through 50) and type 3 queries presented, Figure 8
results. In this graph, 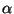 (the amplitude of added noise) is
expressed on the horizontal axis in normalized units.10The bottom group of six curves corresponds to vp-tree performance for
range spaces of increasing dimension. The upper group provides
kd-tree results. It is apparent that vp-tree performance degrades in
a more reasonable fashion for queries increasingly distant from the
data plane.
(the amplitude of added noise) is
expressed on the horizontal axis in normalized units.10The bottom group of six curves corresponds to vp-tree performance for
range spaces of increasing dimension. The upper group provides
kd-tree results. It is apparent that vp-tree performance degrades in
a more reasonable fashion for queries increasingly distant from the
data plane.
Figure 8:
Off Data Plane Queries for Range Spaces of Increasing Dimension.
|
Similar results are obtained given much larger databases and given
databases as simple as a mere line embedded in
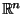 .
.
These results suggest that if one is given a database of unknown
internal structure, the vp-tree may represent a better approach to
organization for nearest neighbor retrieval.
To test the method on a difficult real-world problem, a library of 16
B&W digital images measuring
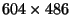 pixels was built. Our
metric space is the set of all fixed size subimages (windows). Sizes
pixels was built. Our
metric space is the set of all fixed size subimages (windows). Sizes
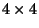 ,
, 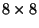 ,
, 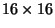 ,
, 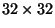 , and,
, and, 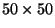 are considered. So for example, a single library image
corresponds to
are considered. So for example, a single library image
corresponds to 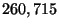 metric space elements of size
metric space elements of size 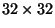 .
.
The Euclidian metric is then applied and nearest neighbor retrieval
effectiveness studied. The vp-trees built were very nearly balanced
although large uniform regions (e.g. the sky) represent pathological
subspaces creating occasional deep subtrees. Databases built from as
many as 8 library images were considered corresponding to a metric
space and vp-tree having over two million members.
For queries from the database, our depth-first branch and bound search reduces
to standard binary tree search and the query is located without
backtracking. Exactly 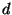 node visits are then required where this refers
to the depth in the tree of the element matching the query.
node visits are then required where this refers
to the depth in the tree of the element matching the query.
For queries even slightly distant from a database member, considerably
more work is necessary. For window size 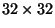 and trees of
roughly one million elements, 5% of the nodes are visited on average
to satisfy very near queries while 15% are visited in the general
case.
and trees of
roughly one million elements, 5% of the nodes are visited on average
to satisfy very near queries while 15% are visited in the general
case.
In one series of experiments we choose subsets of four images each,
and formed vp-trees. Searches were then performed using two query
sources. The first source (general) consisted of a subset of six
images different from each of the database images. The second source
(similar) consisted of a pair of images captured so as to correspond
very closely to a database image in each of the subsets. The results
are summarized in table- 2 where the percentages shown
are averages over the two databases.11
Table 2:
Image Search Results
| Queries |
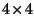 |
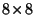 |
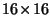 |
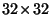 |
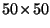 |
| Similar |
1.0% |
3.4% |
4.5% |
4.5% |
5.2% |
| General |
1.4% |
5.7% |
10.7% |
15.7% |
19.3% |
|
Figures 9 and 10 depict 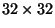 -pixel query/nearest-neighbor pairs for the similar and general
cases respectively.12
-pixel query/nearest-neighbor pairs for the similar and general
cases respectively.12
Figure 9:
A query (left) nearest neighbor pair where the query is drawn from
an image very similar to one in the database.
|
Figure 10:
A query (left) nearest neighbor pair where the query is drawn from
an image entirely different from anything in the database.
|
Limited experiments with
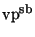 -tree trees result in performance improvements
that vary greatly, but seem to fall in the
-tree trees result in performance improvements
that vary greatly, but seem to fall in the 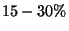 range.
range.
We do not expect the kd-tree to perform well for large windows but perform
experiments to verify our intuition. Indeed, little advantage is
gained over exhaustive search for window sizes as small as 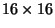 .
.
Reducing search radius 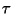 does decrease vp-tree search time but
significant savings are achieved only at the expense of search
effectiveness. In one experiment
does decrease vp-tree search time but
significant savings are achieved only at the expense of search
effectiveness. In one experiment 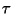 was reduced until search time
was roughly halved. At this radius however, a nearest neighbor was
located for only half of the queries. In another radius related
experiment using single queries, we reduced
was reduced until search time
was roughly halved. At this radius however, a nearest neighbor was
located for only half of the queries. In another radius related
experiment using single queries, we reduced 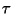 to only slightly
more than the known distance to their nearest neighbor - thus
insuring search success. In one case, the nearest neighbor was
located after only 1200 node visits, with an additional 13,799
required to complete the search. We offer this as illustration that
finding a nearest neighbor and being sure are two separate
matters - with the latter often dominating total cost.
to only slightly
more than the known distance to their nearest neighbor - thus
insuring search success. In one case, the nearest neighbor was
located after only 1200 node visits, with an additional 13,799
required to complete the search. We offer this as illustration that
finding a nearest neighbor and being sure are two separate
matters - with the latter often dominating total cost.
This and other experiments suggest that heuristic search techniques
represent an interesting area for further investigation. Indeed,
independent of its ability to find nearest neighbors and prove
it, the vp-tree method using only the simple search technique
described, seems to very rapidly locate highly similar database
elements. In some applications this may suffice.
Image searches with error tolerance (§3.4) also result in
reduced work. Our limited experiments suggest however that reasonable
tolerance values provide savings of at most perhaps a factor of two.
Finally, independent of search-time refinements, better data
structures and construction techniques, represent a clear opportunity
for future work.
To illustrate the promised generality of our methods, two non-Euclidian
cases are considered: 1) the pseudometric13that arises from normalized correlation. It measures the angle that
two points form with the origin. and, 2) the ordinary Euclidian
vector distance 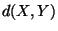 normalized by
normalized by 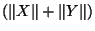 . That the
result is a metric follows from a tedious argument provided in
[27]. In both cases the vp-tree is applied to
randomly constructed databases and exhibits search performance that
corresponds well qualitatively to a standard Euclidian setting.
. That the
result is a metric follows from a tedious argument provided in
[27]. In both cases the vp-tree is applied to
randomly constructed databases and exhibits search performance that
corresponds well qualitatively to a standard Euclidian setting.
We have come to view the vp-tree construction and search processes as
somewhat analogous to standard sort and binary search in one
dimension - first because of their complexity, but perhaps more
importantly because both primarily exploit ordinal rather than
cardinal/representational information.
One may sort a file or build a binary tree of arbitrary objects given
only an appropriate comparison function. By analogy, we have shown that a
metric space may be organized for nearest neighbor retrieval given only the
metric - without consideration of any particular representation such as a
coordinate form. So for example, we will build the same vp-tree for a
database in Euclidian space, independent of coordinate system.
We propose that techniques such as those of this paper should be used
to develop application portable utility software for dynamic
organization of and nearest neighbor retrieval from databases under
application specific metrics.
Finally we observe that both kd-trees and vp-trees may be viewed as very
special cases arising from particular uniformly continuous functionals and
lying within the divide-and-conquer algorithmic paradigm. In one case
coordinate projection, and in the other, distance from distinguished
elements is used to hierarchically decompose space.
I thank Eric Baum, Bill Gear, Igor Rivin, and Warren Smith for
helpful discussions.
- 1
-
J. L. Kelly, General Topology.
New York: D. Van Nostrand, 1955.
- 2
-
B. V. Dasarathy, ed., Nearest neighbor pattern classification techniques.
IEEE Computer Society Press, 1991.
- 3
-
P. N. Yianilos, ``A dedicated comparator matches symbol strings fast and
intelligently,'' Electronics Magazine, December 1983.
- 4
-
P. N. Yianilos, ``New methods for neighborhood searches in metric spaces.''
Invited Talk: The Institute for Defense Analyses, Princeton, NJ, July 23
1990.
- 5
-
J. K. Uhlmann, ``Satisfying general proximity/similarity queries with metric
trees,'' Information Processing Letters, November 1991.
- 6
-
J. K. Uhlmann, ``Metric trees,'' Applied Mathematics Letters, vol. 4,
no. 5, 1991.
- 7
-
W. A. Burkhard and R. M. Keller, ``Some approaches to best-match file
searching,'' Communications of the ACM, vol. 16, April 1973.
- 8
-
K. Fukunaga, ``A branch and bound algorithm for computing k-nearest
neighbors,'' IEEE Transactions on Computers, July 1975.
- 9
-
K. Fukunaga, Introduction to Statistical Pattern Recognition.
Academic Press, Inc., second ed., 1990.
- 10
-
G. Salton and A. Wong, ``Generation and search of clustered files,'' ACM
Transactions on Database Systems, December 1978.
- 11
-
C. D. Feustel and L. G. Shapiro, ``The nearest neighbor problem in an abstract
metric space,'' Pattern Recognition Letters, December 1982.
- 12
-
J. H. Friedman, F. Baskett, and L. J. Shustek, ``An algorithm for finding
nearest neighbors,'' IEEE Transactions on Computers, October 1975.
- 13
-
J. H. Friedman, J. L. Bentley, and R. A. Finkel, ``An algorithm for finding
best matches in logarithmic expected time,'' ACM Transactions on
Mathematical Software, vol. 3, September 1977.
- 14
-
J. L. Bentley and J. H. Friedman, ``Data structures for range searching,'' Computing Surveys, December 1979.
- 15
-
J. L. Bentley, ``Multidimensional divide-and-conquer,'' Communications of the ACM, vol. 23, April 1980.
- 16
-
C. M. Eastman and S. F. Weiss, ``Tree structures for high dimensionality
nearest neighbor searching,'' Information Systems, vol. 7, no. 2, 1982.
- 17
-
B. S. Kim and S. B. Park, ``A fast nearest neighbor finding algorithm based on
the ordered partition,'' IEEE Transactions on Pattern Analysis and
Machine Intelligence, vol. 8, November 1986.
- 18
-
A. J. Broder, ``Strategies for efficient incremental nearest neighbor search,''
Pattern Recognition, vol. 23, no. 1/2, 1990.
- 19
-
R. L. Rivest, ``On the optimality of Elias's algorithm for performing
best-match searches,'' Information Processing 74, 1974.
- 20
-
T. P. Yunck, ``A technique to identify nearest neighbors,'' IEEE
Transactions on Systems, Man, and Cybernetics, October 1976.
- 21
-
F. Aurenhammer, ``Voronoi diagrams - a survey of a fundemental geometric data
structure,'' ACM Computing Surveys, vol. 23, September 1991.
- 22
-
P. M. Vaidya, ``An O(n log n) algorithm for the
all-nearest-neighbor problem,'' Discrete & Computational Geometry,
vol. 4, no. 2, pp. 101-115, 1989.
- 23
-
K. L. Clarkson, ``A randomized algorithm for closest-point queries,'' SIAM
Journal on Computing, vol. 17, August 1988.
- 24
-
K. L. Clarkson, ``New applications of random sampling in computational
geometry,'' Discrete & Computational Geometry, vol. 2, pp. 195-222,
1987.
- 25
-
A. M. Frieze, G. L. Miller, and S.-H. Teng, ``Separator based parallel divide
and conquer in computational geometry,'' SPAA 92, 1992.
- 26
-
D. Dobkin and R. J. Lipton, ``Multidimensional searching problems,'' SIAM
Journal on Computing, vol. 5, June 1976.
- 27
-
P. N. Yianilos, ``Normalized forms for two common metrics,'' tech. rep., The
NEC Research Institute, Princeton, New Jersey, December 1991.
Data Structures and Algorithms for Nearest Neighbor Search in
General Metric Spaces
This document was generated using the
LaTeX2HTML translator Version 2K.1beta (1.47)
Copyright © 1993, 1994, 1995, 1996,
Nikos Drakos,
Computer Based Learning Unit, University of Leeds.
Copyright © 1997, 1998, 1999,
Ross Moore,
Mathematics Department, Macquarie University, Sydney.
The command line arguments were:
latex2html -split 0 -image_type gif -nonext_page_in_navigation -noprevious_page_in_navigation -up_url ../main.html -up_title 'Publication homepage' -numbered_footnotes vptree.tex
The translation was initiated by Peter N. Yianilos on 2002-07-07
Footnotes
- ... 1986-871
-
First coded and tested in July of 1987 during a
Proximity Technology Inc. company workshop in
Sunnyvale California. Participants in addition to the
author were Samuel Buss (then at U.C. Berkeley/Mathematics), Mark
Todorovich, and Mark Heising.
- ... relation2
-
Bounded metrics may simply be scaled.
Unbounded metrics may be adjusted using the well
known formula:
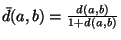 .
.
- ... generality3
-
The method of compression may affect search
efficiency/time, but not the result.
- ... drawn4
-
We can do this in general by choosing the smallest
sigma-algebra containing the space's metric topology,
and defining a measure on it.
- ... returned.''5
-
- ... tree7
- And we've not considered the issue of median
ambiguity.
- ... vp-tree8
-
In all of our experiments, fixed sample sizes are employed to
choose and evaluate vantage points. In hypercube settings, we
evaluate
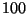 random vantage point candidates by computing
their distance to
random vantage point candidates by computing
their distance to 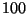 random database elements. For image
experiments, only
random database elements. For image
experiments, only 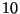 candidates are drawn.
candidates are drawn.
- ... node9
- There are 4,000
total.
- ... units.10
-
The unit consists of the average distance from a type 1 query
to its nearest neighbor. So
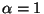 then corresponds to
added
then corresponds to
added 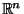 noise of comparable amplitude.
noise of comparable amplitude.
- ... databases.11
-
Our use of a pair of databases represents a crude statistical
precaution necessary due to the small number of images
we can computationally afford to deal with. Despite this
measure, and our careful attempts to build a varied image set,
we are mindful of the fact that the entire space of naturally
occurring images is immense indeed in comparison with our
experiments. One should therefore not conclude that
the statistics we report are representative of the fully
general case.
- ... respectively.12
- The value displayed in these figures
represents Euclidian distance between the query/database-element
pair.
- ... pseudometric13
-
Our methods have been presented for metric spaces only but may
be generalized to pseudo-metric spaces.
Up: Publication homepage
Peter N. Yianilos
2002-07-07
![]() time, and search is under certain circumstances and in the
limit,
time, and search is under certain circumstances and in the
limit, ![]() expected time.
expected time.